Manage360 Cybersecurity from CRA
IT Security NYC
Safeguarding enterprises for more than three decades through cutting-edge IT security in NYC
Cybersecurity threats can originate from various directions, including hacktivists, corporate spies, malware and phishing scams, botnets, and even script kiddies! No matter the type of threat or where it originated, cyber threats can leave both employees and the company at risk. Luckily, you can avert such threats by adhering to a proactive cybersecurity practice with the help of one of the most experienced cyber security companies in NYC.
At Computer Resources of America, we provide solutions that not only anticipate threats, but we also mitigate the risks before they cause irreparable damage to IT systems and business reputations. We aim to keep businesses safe, secure, operational, and compliant, irrespective of threat intensity – and we do this by following a set mechanism. We help companies manage various security risks involving assets, systems, and data. In addition, a CTA cyber security specialist can help businesses express the overall management of cybersecurity risks by organizing data, addressing threats, enabling risk management decisions, and more.
We even help develop and apply the necessary activities to detect cybersecurity occurrences and provide essential means to respond to them so that companies can quickly recover. Read on to learn more about one of the best and most reliable cyber security companies NYC has to offer.

Ready to find out more?
Drop us a line today for a free evaluation!
The Top IT Security Company in NYC
Computer Resources of America (CRA) provides award-winning managed IT support and solutions to mid-size businesses, non-profits, government agencies, and financial services companies in New York City and the surrounding area. Here’s a more detailed look at how our services work.
For instance, if you want to prevent and detect threats on networks, users, and endpoints, you can set prompts for each identified risk. This will cause an automated investigation flow to kick in, revealing the attack’s origin and cause, and automatically fixing the issue.
Our Manage, Detection, and Response Team (MDR) works around the clock 24/7 to monitor and optimize this process for instant resolutions.
- Automate any compliance and/or risk assessment against any framework or standard
- Harmonize compliance requirements, allowing teams to remediate once and gain credit for many, and automation to map once and fulfill many controls
- Manage risks dynamically as they are updated in real-time and foster a risk-aware culture
- Leverage data coming from the security tech stack to automate compliance and update risks via integrations with vulnerability management platforms, threat intelligence platforms, SOAR, IAM, CWPP, Cloud Infrastructure, and more
- Measure return on Security Investment (ROSI) and standardize on risk quantification methodologies such as FAIR, NIST 800-30
- Generate automated reporting such as Plan of Action and Milestones (POAM), System Security Plan (SSP), Risk Assessment (RA), and NIST Scorecards, among others
- Illustrate compliance and risk posture, gaps, and initiatives for improvement with fully customizable Governance Dashboards
- Optimize resources across people, processes, and technology with solution-cost modeling
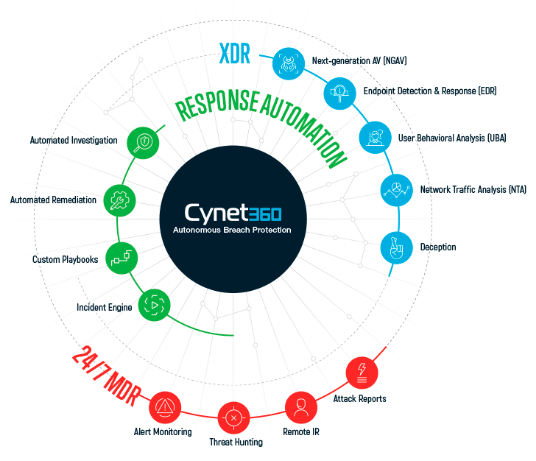
The Power of Manage360:
Continuous, Logical, and Always Learning
Cyberthreats are rising and endlessly targeting companies with endpoint, user, and network-based attacks. Complete protection from such threats involves the operation and deployment of numerous security products by skilled teams, which is excessively complex to function. What to do now? Choose the world’s first-ever “Autonomous Breach Protection” – that integrates network, user, and endpoint detection and prevention of XDR along with auto-remediation and investigation.
Here are a few key benefits:
- A single solution to safeguard from various threats, including network and user as well as endpoint attacks
- Zero-touch security from advanced and common threats
- Provides complete defense on cloud and premises workloads
- Offers additional protection by bringing in seasoned security experts
- Drastically reduce time put in management and deployment

Autonomous Breach Platform Capabilities
The autonomous breach platform is purpose-made to provide total protection based on three key pillars: detection and prevention of all advanced and common threats, complete automation of response flow from detection to eradication of malicious activities, and continuous tracking of the process by skilled professionals to guarantee and raise the quality and precision of the procedure.
Trending Resources

The Importance Of Having A Cybersecurity Culture In Your Workforce

Your Complete Prep Guide to Cybersecurity in 2021 and Beyond

Protect Your Data Against Ransomware Attacks
Cybersecurity as a Service NYC Businesses Can Rely On

Firewall
Network security device that monitors incoming and outgoing network traffic, and permits or blocks data packets based on a set of predetermined security rules. Its purpose is to establish a barrier between your internal network and incoming traffic from external sources (such as the internet) in order to block malicious traffic like viruses and hackers.

Power Filtering
Power filtering involves the use of devices to protect electronic equipment from power surges, spikes, and electromagnetic interference. Computer Resources of America can install and maintain power filtering solutions to ensure the reliability and longevity of critical IT infrastructure.

Cybersecurity Training
Cybersecurity training is essential for educating employees about the latest threats, safe online practices, and how to recognize and respond to potential security incidents. We offer customized training programs to help businesses reduce the risk of human error and insider threats.

Next-Gen AV
(NGAV)
Next-generation antivirus solutions go beyond traditional signature-based detection to incorporate advanced techniques such as machine learning, behavioral analysis, and exploit prevention. CRA deploys and manages these solutions to provide more comprehensive protection against evolving malware and zero-day threats.

Endpoint Detection
and Response
Endpoint Detection and Response (EDR) solutions offer real-time monitoring and analysis of endpoint activities to detect and respond to threats. By implementing EDR, we can provide continuous visibility into endpoint behavior, enabling rapid detection and response to potential security incidents.

User Behavior
Analytics
User Behavior Analytics tools analyze user activities and behavior patterns to identify anomalies that may indicate a security threat, such as compromised credentials or insider threats. Our managed IT services leverage UBA to enhance security monitoring and threat detection capabilities.
Network Traffic Analysis
Network Traffic Analysis (NTA) solutions analyze network traffic to detect and investigate security threats, including malware infections, data exfiltration, and unauthorized access. Computer Resources of America uses NTA to gain insights into network activities and identify potential security issues.

Deception
Deception technology involves creating traps and decoys within the network to detect and divert attackers away from valuable assets. We deploy deception solutions to create a proactive defense layer, making it more difficult for attackers to navigate the network undetected.
CRA: Leading the Pack Among Cyber Security Companies in NYC
Computer Resource of America is widely recognized as a leading managed IT service provider in New York City, with its reputation built on several key factors that set it apart from its competitors.
CRA boasts an extensive portfolio of services catering to a wide range of IT needs, from cloud solutions and cybersecurity to IT consulting and managed services. Our comprehensive approach ensures that businesses of any size can find all the IT support they need under one roof, streamlining their operations and reducing the complexity of managing multiple vendors.
In addition to the technical expertise, CRA's commitment to customer service is second to none. We understand the unique challenges and demands of operating in the fast-paced New York City business environment and, as such, offer personalized service and tailored solutions to meet each client's specific needs. Our customer-centric approach has earned us a loyal client base and a reputation for reliability and excellence.
Our team of experts is another critical factor in CRA’s success. We employ highly skilled and experienced professionals who are well-versed in the latest technologies and industry best practices. Their expertise enables CRA's clients to receive cutting-edge solutions and proactive support, helping them stay ahead of the curve in a competitive market.
Not only that, but CRA's focus on innovation and staying ahead of technological advancements is evident in its adoption of next-gen technologies like cloud computing, cybersecurity, and data analytics. By leveraging these technologies, we help our clients enhance their efficiency, security, and competitiveness.
CRA’s proven track record of delivering successful projects and its ability to adapt to the evolving IT landscape has cemented its position as a leader in the industry. With a strong foundation built on expertise, innovation, and customer satisfaction, Computer Resource of America continues to set the standard for managed IT services in New York City.
Looking for an IT security company in NYC? Get started today with Computer Resources of America (CRA). Contact us for more information.

