Complete IT Compliance Checklist for NYC Law Firms (2026 Edition)
Law firm IT compliance protects your practice from ethical violations, data breaches, and regulatory penalties. NYC law firms face unique technology obligations under state bar rules, grievance committee oversight, and strict cybersecurity regulations. Whether you manage a small practice or a large firm, understanding these requirements is not optional anymore.
In 2026, NYC law firms must meet specific technology competence standards under NY Rules of Professional Conduct (RPC) 1.1(c) and Rule 1.6, which require reasonable efforts to prevent unauthorized access to client information. These rules make cybersecurity a professional duty, not just an IT concern. The Attorney Grievance Committee (AGC) now scrutinizes technology infrastructure during investigations to verify compliance. Firms that fail to meet these standards risk disciplinary action, malpractice claims, and loss of client trust.
This guide covers everything you need to know about law firm IT compliance in 2026. You'll learn about ethical technology requirements, cybersecurity mandates, client confidentiality protocols, and NYC-specific e-discovery rules. We'll also provide practical checklists and actionable steps to help your firm stay compliant and secure.
Key Takeaways
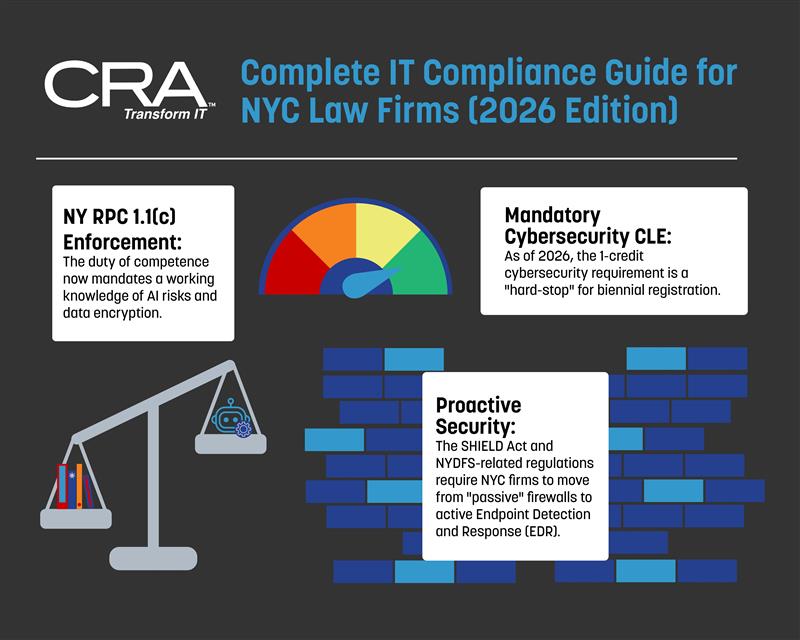
- NY RPC 1.1(c) Enforcement: The duty of competence now mandates a working knowledge of AI risks and data encryption.
- Mandatory Cybersecurity CLE: As of 2026, the 1-credit cybersecurity requirement is a "hard-stop" for biennial registration.
- Proactive Security: The SHIELD Act and NYDFS-related regulations require NYC firms to move from "passive" firewalls to active Endpoint Detection and Response (EDR).
Fundamentals of Law Firm IT Compliance in NYC
Law firm IT compliance in NYC requires adherence to specific technology standards set by the New York State Unified Court System, the New York State Bar, and federal regulations that protect client data and maintain attorney-client privilege in digital environments.
Defining Law Firm IT Compliance Standards
Law firm IT compliance standards establish the minimum technology requirements your firm must meet to protect client information and maintain ethical obligations. These standards come from multiple sources including the NY Rules of Professional Conduct, state bar associations, and industry-specific regulations like the SHIELD Act.
The NY RPC 1.6(c) requires you to "make reasonable efforts to prevent the inadvertent or unauthorized disclosure of, or unauthorized access to, information relating to the representation of a client." This means you must implement appropriate security measures for all systems that store or transmit client data. In 2026, "reasonable efforts" is legally interpreted to include Multi-Factor Authentication (MFA) and AES-256 encryption.
Core compliance standards include:
- Encryption requirements for data at rest (hard drives/cloud) and in transit (email/portals).
- Access control protocols limiting who can view sensitive files based on the "principle of least privilege."
- Audit logging systems tracking data access and modifications to detect internal threats.
- Incident response procedures for potential breaches, mandated by the NY SHIELD Act.
- Regular security assessments identifying vulnerabilities in remote work setups and office networks.
New York's Rules of Professional Conduct 1.6 mirrors the ABA requirements but adds state-specific obligations. Your firm must document all technology safeguards and maintain records proving compliance efforts, especially as the AGC now requests these documents during disciplinary inquiries.
Importance of Legal Compliance for NYC Law Firms
Legal compliance protects your firm from multiple risks that threaten both your practice and your clients. Data from early 2026 shows that 32% of mid-sized law firms experienced a security event in the previous year, with average costs exceeding $5 million for affected practices when accounting for forensic costs and reputational damage.
NYC law firms face heightened scrutiny due to the volume of high-value clients and transactions handled in the city. The Attorney Grievance Committee now treats technology failures as a potential breach of Rule 1.1 (Competence) and Rule 5.3 (Supervision of Non-lawyers).
Your compliance efforts directly affect client retention. Recent data shows 37% of corporate clients will pay premium rates for firms demonstrating strong cybersecurity practices (ISO 27001 or SOC 2 compliance), while 66% prefer working with technologically advanced practices that offer secure client portals over email.
Regulatory Compliance Frameworks Applicable to Law Firms
NYC law firms must navigate overlapping regulatory frameworks that each impose specific technology requirements. Your compliance obligations depend on your client base and practice areas.
Primary Frameworks for 2026:
- NY Rules of Professional Conduct: State-specific confidentiality and competence obligations (Rules 1.1, 1.6, 5.1, 5.3).
- NY SHIELD Act: Mandatory for firms collecting private information (SSNs, Biometrics, Credit Cards) from NY residents. It requires a Written Information Security Policy (WISP).
- HIPAA: Applies when handling Protected Health Information (PHI) in medical malpractice, personal injury, or healthcare cases.
- CCPA/CPRA & GDPR: Necessary when representing clients with ties to California or the EU.
- NYDFS 23 NYCRR 500: While primarily for financial institutions, NYC firms serving as "Third-Party Service Providers" to banks must meet these rigorous cybersecurity standards.
The SHIELD Act specifically requires you to implement:
- Administrative safeguards: Designating an employee to coordinate the security program and training staff.
- Technical safeguards: Network security, software monitoring, and secure data disposal.
- Physical safeguards: Controlling access to servers and paper files.
If your firm handles credit card payments, PCI DSS 4.0 compliance is mandatory. Furthermore, firms working with international financial sector clients may fall under DORA (Digital Operational Resilience Act) requirements, which mandate comprehensive ICT risk management and incident reporting protocols for firms supporting the financial ecosystem.
Ethical Obligations and Rules for Technology Use
New York attorneys must meet specific technology competence requirements under the state's professional conduct rules. These obligations require lawyers to understand relevant technology, protect client data through proper security measures, and maintain confidentiality when using digital tools and AI platforms.
NY RPC 1.1(c) Technology Competence Requirements
NY Rule 1.1(c) requires you to provide competent representation, which includes staying current with changes in technology and the associated risks. In 2026, this specifically includes the risks of Generative AI.
You must evaluate the sensitivity of client information before choosing how to store or transmit it. Highly confidential matters—such as M&A details or intellectual property—require stronger security measures than routine communications. Your duty includes keeping current with "Zero-Day" vulnerabilities and ensuring your software is not "End of Life" (EOL).
The rule applies to all technology you use:
- Email: Must be encrypted for sensitive attachments.
- Cloud Storage: Must have a Business Associate Agreement (BAA) or equivalent security guarantee.
- Mobile Devices: Must have remote-wipe capabilities and encrypted storage.
- AI Tools: Must be "Enterprise" instances where data is not fed back into public training models.
NY Rule 1.6 and Confidentiality in the Digital Age
New York Rule 1.6 imposes strict confidentiality obligations that extend to all digital communications. You must protect client information from unauthorized disclosure regardless of the technology platform you use.
Your confidentiality duty covers information gained during representation, including emails, text messages, video calls (Zoom/Teams), and documents stored electronically. You cannot discuss client matters on unsecured devices or in public settings where smart speakers or unauthorized individuals might intercept communications.
When choosing technology tools, you need to assess their security features. Free or consumer-grade applications (like "Basic" Dropbox or personal Gmail) often do not provide the data privacy levels required for attorney-client privilege protection.
Law Firm Cybersecurity Requirements
Law firm cybersecurity starts with three core technical controls that protect client data and meet 2026 compliance standards. You need proper access management, strong authentication methods, and ongoing system protection.
Access Controls and Role-Based Permissions
Access controls limit who can view and modify sensitive client information. You should implement Role-Based Access Control (RBAC) that gives each employee access only to the files and systems they need for their specific job function.
- Associates should not have access to firm-wide billing and payroll systems.
- Administrative staff do not need access to every litigation case file.
- Just-in-Time (JIT) Access can be used for temporary staff or contractors.
Track who accesses what information and when. These audit logs help you spot "Insider Threats" and prove compliance during security reviews. NYC law firms must maintain these records to meet state cybersecurity requirements.
Multi-Factor Authentication (MFA) Standards
MFA requires two separate forms of verification. In 2026, the standard has moved away from SMS (text) codes to Authentication Apps (TOTP) or Hardware Keys (YubiKey).
You must enable MFA on these systems:
- Email accounts (the #1 vector for law firm hacks).
- Document management software (NetDocuments, iManage).
- Case management platforms (Clio, MyCase).
- Remote access tools (VPN/Remote Desktop).
- IOLTA/Trust Account banking and payment systems.
New York cyber insurance providers now require MFA for coverage. Many firms fail their initial insurance reviews because they haven't implemented it properly across all user accounts, including partners.
Endpoint Protection, Automated Patching, and Vulnerability Scans
Endpoint protection software (EDR) defends every device that connects to your network. You need more than just traditional antivirus; you need AI-driven behavior monitoring to stop ransomware before it encrypts files.
Automated Patching: Security patches fix vulnerabilities that hackers exploit. In 2026, the "Exploit Gap" (the time between a patch release and a hack) is measured in hours. Your firm should install critical security patches within 24–48 hours of release.
Vulnerability Scans: Run these scans at least monthly. They identify "shadow IT" (unauthorized devices) and weak points in your network before attackers find them.
Your endpoint protection should include:
- Real-time threat detection and automated isolation.
- Ransomware protection that can "roll back" encrypted files.
- Web filtering to block malicious "phishing" sites.
- Mobile Device Management (MDM) for attorneys working from home or court.
NYC Bar, Grievance Audits, and Local Oversight
New York law firms face regular technology oversight. These bodies can investigate technology failures that compromise client confidentiality and require lawyers to complete continuing legal education on digital security.
Attorney Grievance Committee Technology Reviews
The AGC reviews complaints about attorneys who fail to protect client data. When investigating technology-related violations, the committee examines your firm's email security, file storage systems, and data breach response protocols.
You can face disciplinary action if the committee finds that technology failures led to unauthorized disclosure. The committee has the authority to issue private admonitions or public censure. Your firm should maintain Compliance Documentation showing regular security updates, employee training records, and incident response plans. The committee considers whether you took "reasonable steps"—the standard is not perfection, but proactive diligence.
Continuing Legal Education (CLE) on Cybersecurity
New York now requires attorneys to complete one (1) credit hour of CLE in Cybersecurity, Privacy and Data Protection as part of their 24-credit biennial requirement.
The NYC Bar Association and other providers offer programs on:
- Recognizing sophisticated "Deepfake" phishing attempts.
- Securing mobile devices in public spaces like the NYC Subway or Courts.
- Evaluating the ethics of AI in legal research and drafting.
You must complete this credit to remain in good standing. Many programs now address Rule 1.15 (Escrow) security, as hackers increasingly target real estate closings and litigation settlements.
Safeguarding Client Confidentiality and Secure Communication
Law firms must protect client confidentiality through specific technology safeguards. These include encryption tools, secure file sharing platforms, and regular employee training.
Client Confidentiality Technology Checklist
- [ ] Risk Assessment: Identify where sensitive information lives (Servers, Cloud, Local Laptops).
- [ ] Encryption: Ensure all laptops and mobile devices use Full Disk Encryption (FDE).
- [ ] Access Logs: Turn on logging for your Document Management System.
- [ ] WISP: Ensure your Written Information Security Policy is updated for 2026 threats.
Secure Client Communication and File Sharing
Email remains a common weak point. Standard email sends messages in plain text. You need Encrypted Email or Secure Client Portals for all communications containing PII (Personally Identifiable Information) or sensitive case strategy.
Avoid using consumer-grade tools like personal Dropbox or Gmail for client matters. These services lack the security controls required for attorney-client privilege protection and often do not offer the Business Associate Agreements necessary for HIPAA compliance.
Phishing Simulations and Security Awareness Training
Human error causes most data breaches at law firms. Run phishing simulations monthly to test your staff. Use the results to identify employees who need additional training.
Focus on 2026-specific threats:
- Business Email Compromise (BEC): Hackers posing as partners asking for urgent wire transfers.
- Vishing/Smishing: Voice or text-based phishing attempts.
- QR Code Phishing: Malicious links hidden in QR codes.
Operational and Financial Compliance Considerations
NYC law firms face strict operational requirements around financial transactions and vendor relationships. These obligations protect client funds and ensure that third-party providers meet security standards.
Trust Accounting, IOLTA, and Payment Processor Standards
You must keep client funds separate under NY RPC 1.15. Your trust accounting software needs:
- Three-way reconciliation reports.
- Audit trails that track every deposit and withdrawal.
- MFA protection on all banking logins.
Payment processors must be PCI compliant and should tokenize card data so your firm never stores actual credit card numbers.
Vendor and Third-Party Risk Management
Every vendor (IT, Cloud, AI, E-Discovery) creates compliance risk. You need written agreements specifying their security obligations. Before signing, review their SOC 2 Type II reports or ISO 27001 certifications. Your agreements should require vendors to notify you within 24 hours of any security incident.
Building a Resilient Technology Infrastructure
NYC law firms must maintain systems that protect client data during both routine operations and crisis situations.
Data Backup, Disaster Recovery, and Business Continuity
You need the 3-2-1 Backup Rule:
- 3 copies of your data.
- 2 different media types (Cloud and Local).
- 1 copy stored Offline/Immutable (to prevent ransomware from deleting your backups).
Test your recovery process quarterly. Your clients need to know you can recover their files within specific timeframes. Create a Business Continuity Plan that identifies how you will work if your Manhattan office is inaccessible.
NYC-Specific Compliance Risks and E-Discovery
E-Discovery Technology Requirements for NYC Law Firms
For firms in the NY Supreme Court Commercial Division, compliance with Rule 11-c is mandatory. You must be prepared to "meet and confer" regarding:
- The scope of ESI (Electronically Stored Information).
- Data formats and metadata preservation.
- The use of Technology-Assisted Review (TAR) or AI for document review.
Mitigating Emerging IT Risks Unique to New York
NYC firms are high-value targets for "Nation-State" actors seeking intellectual property or sensitive business data. Your security must account for this elevated threat profile. Additionally, NYDFS regulations often trickle down to law firms that represent financial institutions, requiring a higher tier of security than a standard business.
Final Compliance Checklist for 2026
- Is your MFA enabled on everything?
- Have you completed your Cybersecurity CLE credit?
- Do you have an updated WISP that includes an AI policy?
- Are your IOLTA accounts protected by dedicated secure hardware?
Important Legal Disclaimer
General Information Only: The information provided in this article is for general informational and educational purposes only. It does not constitute legal, financial, or professional compliance advice. While Computer Resources of America strives to ensure the accuracy and timeliness of the information presented as of the publication date, the regulatory landscape—including New York Rules of Professional Conduct, the NY SHIELD Act, and CLE requirements—is subject to frequent change and varying interpretations by courts and ethics committees.
No Professional Relationship: Your use of this website or the information contained in this blog post does not create a professional relationship between you and Computer Resources of America. We are an IT services provider, not a law firm. Compliance with the New York Rules of Professional Conduct is the sole responsibility of the licensed attorney.
Fact-Checking and Accuracy: While we make every effort to provide comprehensive guides, Computer Resources of America makes no representations or warranties of any kind, express or implied, about the completeness, accuracy, or reliability of the information, statistics, or legal citations contained herein. Laws and technical standards in 2026 are evolving rapidly; therefore, any reliance you place on such information is strictly at your own risk.
Limitation of Liability: In no event will Computer Resources of America be liable for any loss or damage, including without limitation, indirect or consequential loss or damage, or any loss or damage whatsoever arising from loss of data, disciplinary actions, or malpractice claims arising out of, or in connection with, the use of this guide.
Consult a Professional: We strongly recommend that NYC law firms consult with their own legal counsel, ethics advisors, or the New York State Bar Association to confirm their specific compliance obligations. Technology implementations should always be tailored to a firm’s unique risk profile by a qualified IT professional.
