Q1 Threat Intelligence Report: Cybersecurity Threats Targeting NYC Law Firms & Financial Advisors in 2026
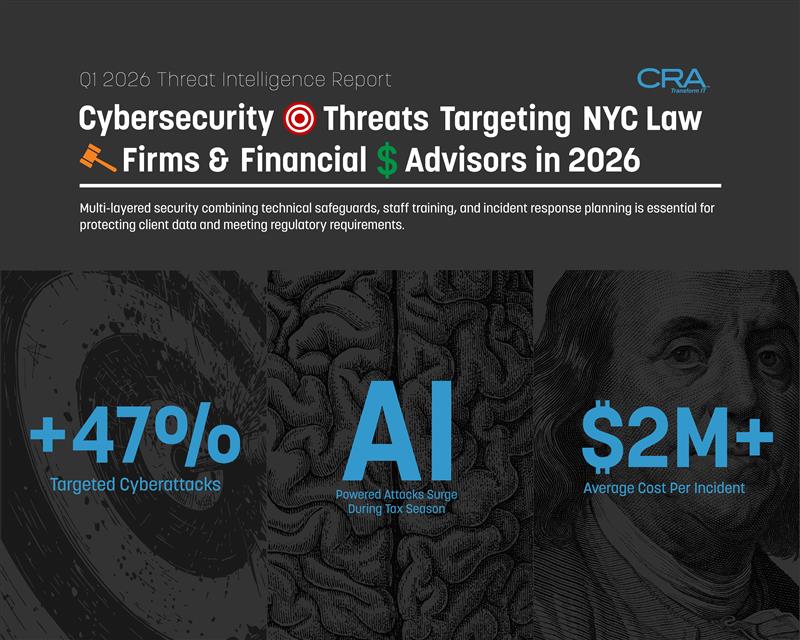
Law firms and financial advisors in New York City are facing their most dangerous quarter yet. In the first six weeks of 2026, cybercriminals launched targeted attacks against professional services firms at rates 47% higher than the same period last year, with average ransom demands reaching $2.3 million for law firms and breach costs averaging $4.1 million for financial advisory practices. These numbers tell a clear story: your firm holds exactly what attackers want—sensitive client data, access to financial accounts, and the regulatory pressure that makes you more likely to pay.
The threat landscape has shifted in ways that make traditional security measures insufficient. Attackers now use AI-powered tools to craft convincing phishing emails, exploit trusted third-party vendors, and identify the exact moment when your staff is most vulnerable. Tax season creates additional pressure for financial advisors, while litigation deadlines put law firms in high-stress situations where mistakes happen. Cybercriminals know this and time their attacks accordingly.
This Q1 threat intelligence report breaks down the specific attack methods targeting NYC law firms and financial advisors right now. You'll learn which ransomware variants are actively circulating, how business email compromise schemes have evolved, and where your firm's biggest vulnerabilities likely exist. Most importantly, you'll understand what you need to do this quarter to protect your clients and your practice.
Key Takeaways
- Law firms and financial advisors face 47% more targeted attacks in early 2026 compared to last year, with average costs exceeding $2 million per incident
- Attackers now use AI-powered tools and exploit tax season pressure to target professional services firms when they are most vulnerable
- Multi-layered security combining technical safeguards, staff training, and incident response planning is essential for protecting client data and meeting regulatory requirements
2026 Q1 Cybersecurity Threats: NYC Law Firms and Financial Advisors
NYC law firms and financial advisors faced a sharp increase in cyberattacks during the first months of 2026, with multiple data breaches reported in January alone. The attacks exploited known vulnerabilities during the busiest operational periods for both industries, creating urgent pressure to strengthen defenses before losses escalate.
Recent Data Breaches: What Happened in NYC
Three NYC law firms and five financial advisory firms reported significant data breaches in January 2026. These incidents shared common attack vectors, including compromised email accounts and unpatched vulnerabilities in third-party software.
One mid-sized law firm experienced a ransomware attack that encrypted case files and client communications. The attackers demanded $450,000 and threatened to publish sensitive legal documents on the dark web. Initial investigation revealed the breach started with a phishing email that targeted a junior associate.
A financial advisory firm lost access to client portfolios and tax documents after a Business Email Compromise attack. The criminals used AI-generated voice messages to trick staff into transferring funds and granting system access. Total losses reached $2.3 million, including stolen client assets and recovery costs.
Common vulnerabilities across these breaches included:
- Missing multi-factor authentication on email accounts
- Outdated software on file-sharing platforms
- Insufficient employee training on social engineering tactics
- No formal incident response plan
Urgency for Immediate Action During Tax and Litigation Season
Tax season creates heightened risk for financial advisors as they handle increased volumes of sensitive financial data. Criminals know that firms face pressure to process returns quickly, making staff more likely to overlook warning signs of phishing attempts.
Law firms entering litigation season manage multiple high-stakes cases simultaneously. This workload increases the attack surface as attorneys share documents with courts, opposing counsel, and expert witnesses. Each file transfer and communication creates potential entry points for attackers.
The NYDFS cybersecurity regulation amendments require covered entities to meet strict compliance deadlines through November 2025, with enforcement active in 2026. Violations can result in significant civil penalties. Financial firms and law practices handling regulated data must demonstrate reasonable security measures to protect client information and maintain client trust.
Delayed action compounds both financial and reputational damage. The average cost of a data breach for professional services firms reached $5.08 million in 2025, with more than half resulting in lost client data.
Key Threat Intelligence Findings for Q1
AI-driven deepfakes emerged as a primary threat targeting legal and financial professionals in early 2026. Attackers use synthetic audio and video to impersonate senior partners or executives, convincing staff to approve wire transfers or share credentials.
Ransomware tactics evolved to include triple extortion. Criminals encrypt data, threaten public exposure, and contact clients directly to pressure firms into paying. Law firm cybersecurity now requires defense against attacks that target reputation alongside technical systems.
Third-party vulnerabilities continue to create cascading risks. E-discovery vendors, document management systems, and client portals have become attractive targets. A breach at one vendor can compromise dozens of firms simultaneously.
Business Email Compromise attacks increased 34% in Q1 2026 compared to Q4 2025. These attacks specifically target periods when firms process high volumes of financial transactions or court filings.
The Current Cyber Threat Landscape in Legal and Financial Services
Professional services firms faced a 47% increase in cyberattacks between 2025 and 2026, with law firms and financial advisors emerging as primary targets due to their high-value data and trust-based client relationships. The convergence of AI-powered attacks, sophisticated ransomware operations, and supply chain vulnerabilities has created an environment where your firm's cybersecurity posture directly impacts client trust and regulatory compliance.
Sector-Wide Attack Trends From 2025 to 2026
The professional services sector experienced significant shifts in attack methods throughout 2025. Ransomware groups adopted double and triple extortion tactics, threatening both data encryption and public exposure of sensitive client files. AI-driven attacks increased by 63%, with threat actors using machine learning to craft convincing business email compromise messages.
Law firms reported that 40% experienced a security breach in the past year, with average incident costs reaching $5.08 million. More than half of these breaches resulted in the loss of sensitive client data. Financial advisory firms faced similar pressures, with attackers targeting wire transfer systems and client account credentials.
Ransomware-as-a-Service (RaaS) platforms democratized cybercrime, allowing less sophisticated attackers to launch complex operations. Supply chain attacks rose sharply as threat actors exploited vulnerabilities in third-party file-sharing platforms, document management systems, and collaboration tools that your firm relies on daily.
NYC-Specific Threat Patterns and Statistics
New York City's concentration of high-value professional services firms makes it a focal point for cybercriminal activity. In January 2026 alone, three NYC law firms and five financial advisory firms reported data breaches, with attackers specifically targeting firms managing high-net-worth client portfolios and active litigation files.
Financial services firms in NYC face heightened exposure during tax season when wire transfer volumes increase and clients share sensitive financial documents. Law firms handling real estate closings, mergers and acquisitions, and intellectual property cases attract targeted attacks due to the immediate financial value of their case files.
Attackers increasingly exploit the geographic concentration of professional services in Manhattan and Brooklyn. They leverage social engineering tactics that reference local landmarks, court systems, and business relationships to increase the credibility of phishing attempts.
Targeting Dynamics: Why Law Firms and Financial Advisors Are in the Crosshairs
Your firm holds exactly what cybercriminals want: confidential client data, financial credentials, and access to funds. Law firm cybersecurity weaknesses provide attackers with privileged information about pending litigation, merger negotiations, and intellectual property that can be sold or used for insider trading.
Financial advisors manage direct access to client accounts and wire transfer capabilities. A successful breach can result in immediate fund transfers before detection, making these firms attractive targets for financially motivated threat actors.
The trust-based nature of your client relationships creates leverage for ransomware operators. The threat of exposing confidential client information or disrupting critical services forces firms to consider ransom payments. Regulatory requirements under ABA Rule 1.6(c) for law firms and SEC cybersecurity rules for financial advisors add compliance pressure that attackers exploit during negotiations.
Your smaller security budgets compared to enterprise organizations make you a softer target. Many professional services firms lack dedicated security staff, rely on outdated systems, and have limited incident response capabilities. This vulnerability, combined with high-value data, creates the perfect target profile for 2026 threat actors.
Top Ransomware and Extortion Threats for Law Firms
Law firms face increasingly aggressive ransomware attacks that specifically target legal files and exploit client confidentiality. Attackers now use multiple extortion methods to maximize pressure on firms to pay.
Ransomware-as-a-Service (RaaS) and Legal File Attacks
RaaS platforms have made sophisticated ransomware accessible to less technical criminals. Groups like LockBit 4.0 and BlackCat provide ready-made tools that scan your network for case files, client documents, and privileged communications. These variants specifically search for common legal file extensions including .docx, .pdf, and practice management software databases.
The attacks typically begin with phishing emails or compromised credentials. Once inside your network, the ransomware moves laterally to identify file servers and backup systems. Your case files become encrypted within hours, and attackers know you face immediate deadlines that create pressure to pay quickly.
Many RaaS operators now offer "customer support" to victims and provide proof-of-decryption samples. They understand law firms cannot function without their files and price ransoms accordingly.
Double and Triple Extortion Schemes
Attackers no longer just encrypt your files. Double extortion involves stealing your data before encryption, then threatening to release it publicly if you don't pay. Triple extortion adds pressure by threatening to contact your clients directly or report you to regulators.
Your client data becomes leverage in multiple ways:
- Public exposure: Attackers threaten to post confidential case details on leak sites
- Client notification: Direct contact with your clients claiming their data was compromised
- Regulatory reporting: Threats to notify state bars or data protection authorities
- Secondary victims: Extorting your clients separately using their stolen information
This approach targets your reputation and client relationships, not just your operations. Even if you restore from backups, the stolen data remains in attacker hands. You need secure file sharing protocols and encryption to limit what attackers can access.
Case Example: NYC Law Firm Ransomware Incident
A midsize Manhattan firm experienced a RaaS attack in late January 2026 through a compromised partner account. The attackers encrypted 47 active case files and exfiltrated 12GB of client data before detection. The firm lacked an incident response plan and delayed containment for 18 hours while debating internally.
The attackers demanded $280,000 and threatened to contact clients directly within 72 hours. The firm paid $150,000 after negotiation but still faced disclosure requirements under New York's SHIELD Act. Three clients terminated their relationships after learning about the breach.
The firm's law firm cybersecurity gaps included no multi-factor authentication on VPN access, infrequent backup testing, and no email security filtering. These basic controls could have prevented or minimized the attack impact.
Emerging Cyber Attack Techniques Targeting Financial Advisors
Financial advisors face distinct threats in 2026 that exploit client trust, high-value transactions, and digital communication channels. Attackers are deploying sophisticated phishing schemes, specialized ransomware, and third-party vulnerabilities to compromise advisory firms and their client assets.
Phishing and Business Email Compromise (BEC)
Credential-driven attacks remain the leading threat vector against financial advisory firms. Phishing emails now use AI-generated content that mimics your communication style, making detection significantly harder for both advisors and clients.
BEC attacks specifically target wire transfer requests and account changes. Attackers compromise your email accounts to intercept client communications, then insert fraudulent payment instructions that appear legitimate. The average BEC loss for financial services firms reached $180,000 in 2025.
Common BEC tactics include:
- Client impersonation requesting urgent wire transfers
- Vendor email compromise altering payment details
- Executive impersonation authorizing fake transactions
- Calendar invite phishing to harvest credentials
Regular phishing simulations help your team identify these evolving tactics. These training exercises expose staff to realistic attack scenarios without actual risk, building recognition skills that reduce successful breach attempts by up to 70%.
Financial Advisor Ransomware Variants
Ransomware groups now deploy variants specifically designed for financial advisory firms. These attacks encrypt client portfolios, tax documents, and compliance records while threatening to leak sensitive financial data to competitors or the public.
The LockBit 4.0 and BlackCat variants use triple extortion. Attackers encrypt your files, threaten to publish client data, and contact your clients directly to pressure you into paying. Ransom demands for advisory firms average $75,000 to $250,000.
Attackers time their strikes during tax season or quarter-end reporting when you face maximum operational pressure. They know you cannot afford downtime during these critical periods. Your incident response plan must include offline backups and secure file sharing alternatives that function independently of your primary systems.
Supply Chain Exploitation in Financial Services
Your technology vendors and service providers create expanding attack surfaces. Hackers compromise portfolio management software, CRM platforms, and cloud storage providers to access multiple advisory firms through a single breach.
Supply chain security vulnerabilities increased 340% in financial services during 2025. Attackers infiltrate trusted software updates, embedding malicious code that activates weeks after installation. The SolarWinds-style attacks now target smaller fintech vendors that lack enterprise-level security.
Critical supply chain risks:
- Portfolio management platform compromises
- Cloud storage provider breaches
- Email service provider vulnerabilities
- Video conferencing software exploits
You must vet every third-party vendor's security practices. Require SOC 2 Type II certifications, conduct regular security assessments, and implement zero-trust architecture that treats all external connections as potentially hostile. Multi-factor authentication should be mandatory for any system accessing client data.
Vulnerabilities and Internal Risks Facing Professional Firms
Professional service firms face significant risks from within their own operations. Employees with legitimate access can become security liabilities through negligence or malicious intent, while poorly managed cloud systems and vendor relationships create exploitable gaps in otherwise strong defenses.
Insider Threats and Credential Theft
Employees and contractors represent one of your firm's biggest security vulnerabilities. A single compromised credential can grant attackers access to client files, financial records, and confidential communications.
Recent data shows that 40% of law firm breaches involve insider actions, whether intentional or accidental. Junior staff often receive phishing emails designed to steal login credentials, while departing employees may retain access to systems weeks after departure.
Common insider threat scenarios:
- Former employees whose access wasn't immediately revoked
- Staff falling victim to credential phishing attacks
- Employees using weak passwords across multiple platforms
- Unauthorized sharing of firm credentials with third parties
You must implement multi-factor authentication across all systems and conduct regular access reviews. Monitor unusual login patterns, especially after-hours access or downloads of large data volumes. Many firms discover breaches only after noticing abnormal employee behavior in system logs.
Misconfigured Cloud and Data Leaks
Cloud storage platforms like SharePoint, Dropbox, and Google Drive create data exposure risks when configured incorrectly. A misconfigured sharing link can expose thousands of client files to anyone with the URL.
Professional firms frequently discover that confidential documents are set to "anyone with link" rather than restricted access. These mistakes often happen when staff prioritize convenience over security during client collaborations.
Your firm should conduct quarterly audits of cloud permissions and file sharing settings. Implement data governance policies that define how different types of client information should be stored and shared. Many breaches occur because firms lack basic visibility into where sensitive data resides.
Third-Party Risk: Vendor and Partner Security
Your security is only as strong as your weakest vendor. Law firms and financial advisors rely on dozens of third-party services for document management, accounting software, case management systems, and client portals.
Supply chain attacks targeting these vendors have increased by 30% since 2025. When an e-discovery vendor or practice management platform gets breached, attackers gain access to data from hundreds of firms simultaneously.
You need to assess vendor security before signing contracts. Require vendors to maintain SOC 2 certification or equivalent security standards. Review their incident response procedures and data handling practices.
Vendor security checklist:
- Request third-party security audit results
- Verify encryption standards for data in transit and at rest
- Confirm vendor's breach notification timeline
- Review data retention and deletion policies
- Assess vendor's own supply chain security measures
Many firms only discover their vendor's poor security after a breach occurs. Establish ongoing monitoring of critical vendors rather than one-time assessments during procurement. Your contracts should include the right to audit vendor security practices and mandate immediate breach notification.
Regulatory Changes, Privacy Laws, and Compliance in 2026
Law firms and financial advisors face tighter reporting deadlines and expanded oversight in 2026. New federal incident reporting rules combine with strengthened state privacy laws to create significant compliance pressure for professional services firms.
NYDFS Cybersecurity Regulation Updates
The New York Department of Financial Services continues to raise the bar for cybersecurity compliance. Financial advisors operating in New York must now maintain enhanced incident response protocols that align with stricter breach notification timelines.
Your firm needs to report cyber incidents faster than before. The updated regulations require detailed documentation of security events, even when client data isn't compromised. This means your incident response plan must include specific notification workflows and pre-drafted templates.
Key NYDFS requirements for 2026:
- Board-level oversight of cybersecurity programs
- Annual penetration testing for firms managing client assets
- Multi-factor authentication across all systems handling sensitive data
- Vendor risk assessments with documented security requirements
Law firms serving financial services clients face indirect pressure from these rules. Your financial advisor clients expect you to meet similar security standards when handling their sensitive information.
National and State Privacy Law Impact
The Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) takes effect in 2026, requiring certain organizations to report serious incidents to CISA within 72 hours. While most law firms and financial advisors don't fall under critical infrastructure definitions, the regulation signals broader federal expectations for incident reporting.
State privacy laws create more direct compliance obligations. California's CCPA updates expand consumer data rights and breach notification requirements. If you serve clients in multiple states, you face overlapping and sometimes conflicting privacy obligations.
Privacy compliance areas demanding attention:
- Data inventories: You must document what client data you collect, where it's stored, and who can access it
- Breach response: State laws impose notification deadlines as short as 14 days after discovery
- Client rights: Your systems need to support data access, correction, and deletion requests
The FTC and SEC are both enforcing stricter data protection standards. Law firm cybersecurity failures that expose client information can trigger regulatory investigations, especially when institutional clients or public companies are affected.
Client and Regulatory Expectations for Cyber Readiness
Your clients increasingly require proof of cybersecurity maturity before sharing sensitive information. Financial advisors managing substantial assets face due diligence requests from institutional clients. Law firms handling high-stakes litigation or M&A transactions encounter similar scrutiny. Regulators expect you to demonstrate continuous security improvement. One-time compliance audits no longer suffice. Your firm needs documented policies, regular risk assessments, and evidence of ongoing employee training.
Professional liability insurers are tightening requirements too. Many policies now mandate specific security controls as conditions of coverage. Without multi-factor authentication, encryption, and documented incident response procedures, you may face higher premiums or coverage exclusions.
Law firms must pay special attention to conflicts of interest that arise from breaches. If your firm's security failure exposes opposing parties' information, you could face disqualification motions and ethics complaints on top of regulatory penalties.
Proven Strategies for Strengthening Law and Financial Firm Cybersecurity
Modern threats require a shift from reactive security to proactive defense systems that assume breaches will happen and build protection at every layer. The following strategies form a practical framework that addresses the specific vulnerabilities facing professional services firms in NYC.
Zero Trust Security Models
Zero trust operates on a simple principle: never trust, always verify. This means every user, device, and application must prove its identity before accessing your systems, regardless of whether they're inside or outside your network perimeter.
Start by implementing identity verification at every access point. Require multi-factor authentication for all applications, not just email. Configure conditional access policies that check device health and location before granting access to sensitive client data.
Segment your network to limit lateral movement. If an attacker compromises one workstation, they shouldn't automatically access your entire file server or case management system. Create separate zones for client data, financial systems, and general business operations.
Apply least-privilege access controls. Your paralegals don't need access to firm banking information. Junior advisors don't need access to all client portfolios. Review permissions quarterly and remove access immediately when employees change roles or leave the firm.
Incident Response Planning and Testing
An incident response plan sits unused in most firms until a crisis hits. At that point, it's too late to figure out who calls the cyber insurance carrier or how to preserve evidence for forensic analysis.
Your plan must identify specific roles and responsibilities. Name the person who makes the decision to shut down systems. List the phone numbers for your IT provider, cyber insurance carrier, forensic specialist, and cyber attorney. Include your state bar's breach notification requirements and client notification templates.
Test your plan twice per year with tabletop exercises. Walk through realistic scenarios: a ransomware attack on Friday at 6 PM, a wire fraud attempt, or a lost laptop containing client files. Time how long it takes to execute each step. Find the gaps before an actual incident exposes them.
Document your communication protocols. Who informs clients? What do you tell them, and when? How do you maintain attorney-client privilege during an investigation? These decisions become exponentially harder under the pressure of an active breach.
Secure File Sharing and Data Governance
Email attachments and consumer file-sharing services create unnecessary exposure for sensitive client information. Your data governance framework must define what information goes where and how it's protected at every stage.
Deploy client portals with end-to-end encryption for document exchange. Solutions like ShareFile, NetDocuments, or Box for Legal provide audit trails showing who accessed what files and when. This visibility matters for both security and compliance.
Classify your data based on sensitivity levels. Mark files containing Social Security numbers, financial account details, or privileged legal communications. Apply encryption and access restrictions automatically based on these classifications.
Establish retention policies that define how long you keep different types of information. Delete data you no longer need. The less data you store, the less you have at risk during a breach. Configure automated deletion for emails older than your retention requirements and closed matter files past your state's requirements.
Continuous Training: Phishing Simulations and Awareness
Your employees represent either your strongest defense or your weakest link. The difference comes down to consistent training that goes beyond annual checkbox compliance sessions.
Run monthly phishing simulations that mimic real-world attacks your firm might face. Test for wire fraud emails, fake court notices, fraudulent vendor invoices, and credential harvesting attempts. Track who clicks and provide immediate coaching, not punishment.
Vary your training content throughout the year. Cover social engineering tactics in January, password security in February, mobile device risks in March. Keep sessions under 15 minutes and make them relevant to your employees' actual work.
Create a culture where reporting suspicious activity is encouraged and easy. Set up a simple way for staff to forward questionable emails to your IT team. Celebrate employees who catch and report attempts. Make security awareness part of your firm's identity, not just an IT department initiative.
Measure improvement over time. Track your click rates on simulated phishing emails. Monitor the number of security incidents reported by employees. These metrics show whether your training investment is working or whether you need to adjust your approach.
